Cybersecurity for Connected Medical Devices: Regulations, Standards, and Technologies in 2025
How Manufacturers Can Meet Regulatory Requirements and Defend Against Cyber Threats
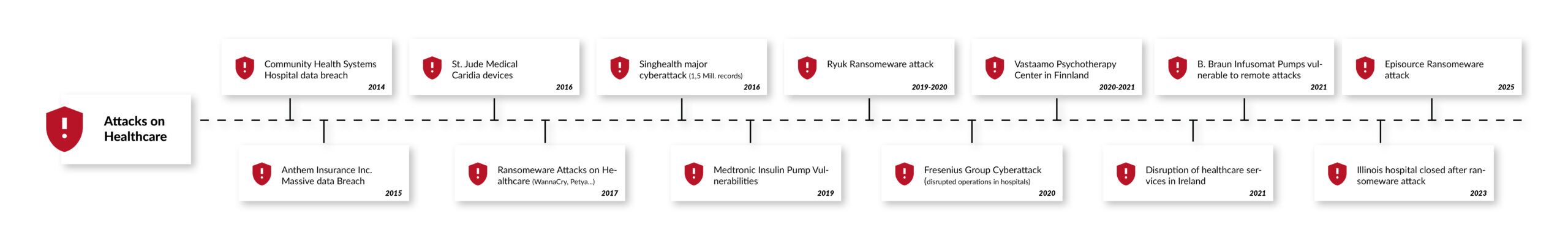
As medical devices become increasingly connected, cybersecurity is critical to protect patient safety and sensitive health data. It is estimated that one in four medical devices is already connected to the Internet or a hospital network. In 2017, their total number was an estimated 337 million, with an expected compound annual growth rate (CAGR) of 20.8% through 2030, including digital health apps, whose development is being driven by the German Digital Healthcare Act (DVG) and similar initiatives across Europe [1]. Digital health apps are increasingly part of health care. Approximately 200 health apps are added to the app stores daily [2]. Any connected medical device or Internet of Medical Things (IoMT) product is a potential target for cyberattacks that can compromise patient or user safety or leak highly sensitive healthcare data. The rapid growth of the Internet of Medical Things (IoMT) and digital health apps has heightened the risk of cyberattacks.
In a recent survey, four out of five medical device manufacturers stated that they had been targeted by at least one cyberattack in 2019 [3]. Other, more recent reports suggest an even darker picture. According to the "2021 Global Threat Intelligence Report" of the technology service company NTT, the number of cybersecurity incidents in the healthcare sector tripled in 2020 compared to the previous year.
Apart from health risks and high penalties for possible data protection breaches, successful cyberattacks or security vulnerabilities that become public can also damage the reputation of manufacturers. The German Federal Institute for Drugs and Medical Devices (BfArM), the U.S. National Cybersecurity and Communications Integration Center (NCCIC), and the U.S. Food and Drug Administration (FDA), for example, provide detailed information about known security risks in medical devices and name the product as well as the manufacturer [4]. Once lost, reputation and trust are difficult to regain, particularly in highly sensitive areas such as healthcare.
This white paper reflects the latest regulatory changes, standards, and technological advancements in medical cybersecurity as of 2025.
Regulatory Landscape
The regulatory environment for medical device cybersecurity has evolved significantly, with both the U.S. and EU introducing updated guidelines to address emerging threats.
European Union Regulations:
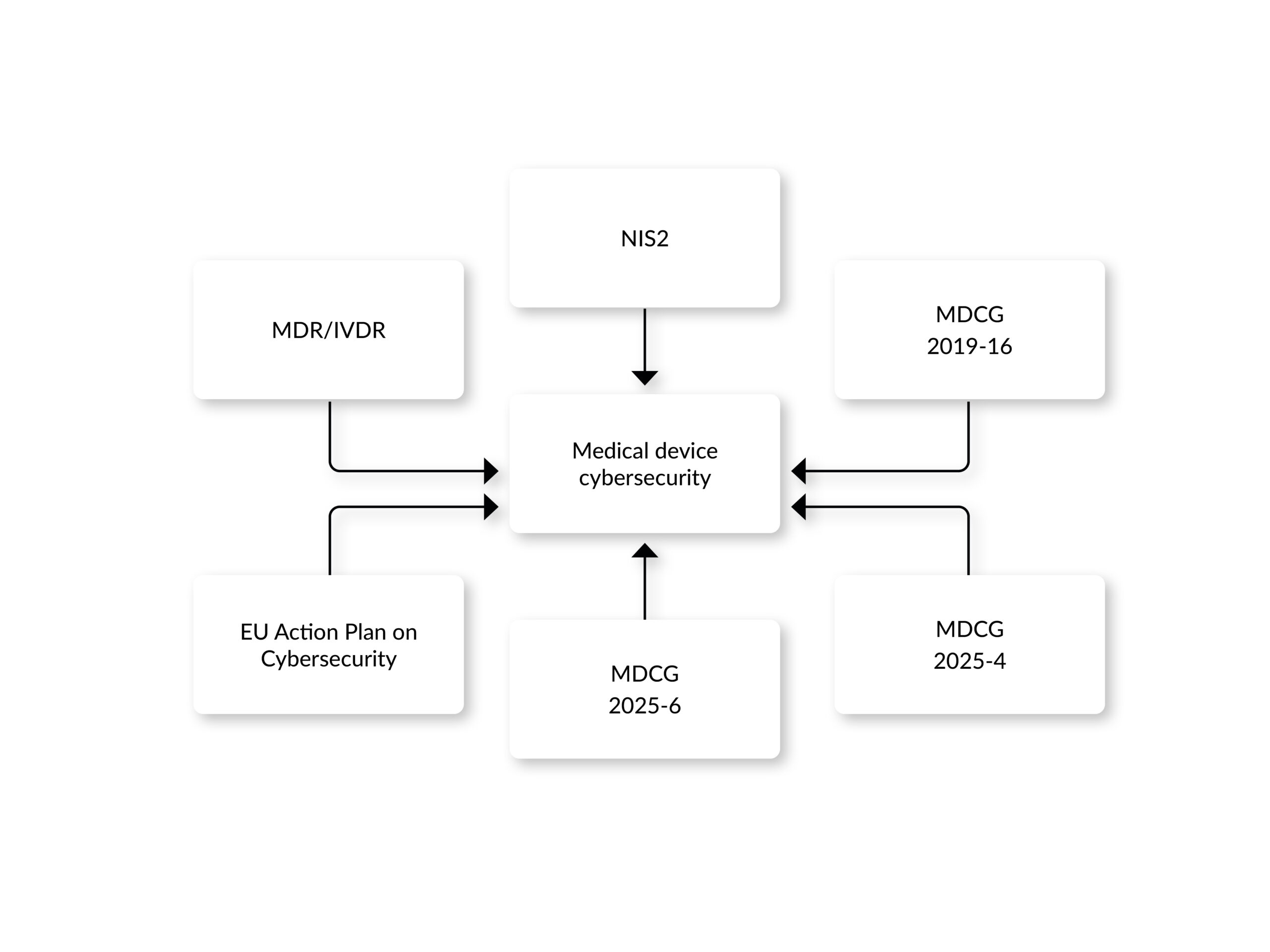
Regulation (EU) 2017/745, also known as the Medical Device Regulation (MDR), provides the regulatory framework for all stakeholders in the medical device market. On May 26, 2021, it repealed the previously valid Directives 93/42/EEC and 90/385/EEC and has since been applied in the countries of the European Union as well as Norway, Iceland, and Liechtenstein. Market access in Europe demands compliance with the general safety and performance requirements defined in Annex I of the regulation. In contrast to the directives, the regulation defines several cybersecurity requirements.
The MDR requires development “according to the state of the art,” considering IT security and the definition of security measures to protect against, e.g., unauthorized access (Annex I 17.2 and 17.4) [7]. This also implies the establishment of a security risk management. The MDCG 2019-16 guidance document further specifies the implementation of a security risk management process. Besides that, the guidance promotes a security-by-design and security-by-default approach, urging cybersecurity considerations to be embedded at every stage of the device lifecycle, from conception through post-market surveillance. New vulnerabilities are usually found after the medical device has been placed on the market. Therefore, risk management should cover the entire life cycle, which includes the decommissioning of the medical device. Among the requirements specifically mentioned in the guidance are a post-market surveillance, an incident response, and a problem resolution process.
While the guidance is very valuable, it could need further refinement and more practical implementation guidance for manufacturers. For instance, a study published in Computational and Structural Biotechnology Journal concludes that it has solid coverage of high-level principles but lacks detail in critical technical areas, such as cryptography, authentication, and secure software development. Other areas, like network security and supply-chain components, receive even less attention [6]. Other researchers outline the lack of real-world implementations for certain aspects of cybersecurity, for instance, establishing baseline requirements for legacy devices, toolkits for threat modelling, and how to align with overlapping frameworks like GDPR, NIS2, and AI Act [7].
Since 2021, additional directives and guidance have strengthened this framework:
- NIS2 Directive (EU) 2022/2555: Effective since January 2023, this directive does not specifically target medical devices; however, it can apply to the organizations that operate or manage networks or systems related to medical devices, if they are considered essential or important entities. For instance, it mandates risk management measures and incident reporting to enhance network and information system security across the EU.
- MDCG 2025-4: Published in June 2025, this guidance outlines requirements for safely distributing medical device software (MDSW) apps on online platforms, clarifying roles for app platform providers under the MDR, IVDR, and Digital Services Act (DSA). The guidance requires the specification of requirements for cybersecurity in medical device software.
- MDCG 2025-6: Released in June 2025, this FAQ-style document addresses the interplay between the MDR, IVDR, and the Artificial Intelligence Act, and among others, emphasizing cybersecurity considerations for AI-enabled devices.
- EU Action Plan on Cybersecurity: Launched in January 2025, the European Commission launched a plan aimed at improving the cybersecurity of hospitals and healthcare providers, including connected medical devices, by establishing a pan-European Cybersecurity Support Centre.
United States Regulations:
In the U.S., the Food and Drug Administration (FDA) has significantly updated its cybersecurity oversight over the past few years:
- The FDA guidance “Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions” was updated in 2025 with clarifications on the term „cyber device“ and contains recommendations on device design, labeling, and documentation for premarket submissions, including requirements for a Software Bill of Materials (SBOM) and post-market vulnerability management plans. The FDA’s guidance emphasizes a Secure Product Development Framework (SPDF) to reduce vulnerabilities throughout the device lifecycle, aligning with global best practices. Despite being a US FDA guidance and focusing on compliance with FDA requirements, it’s a highly recommended literature for a pragmatic and at the same time effective implementation of cybersecurity in a medical device, even for those not targeting the US market.
- Section 524B of the FD&C Act: This law was updated by the omnibus bill, which was signed into law in December 2022, and added section 3305 with „Ensuring cybersecurity of devices“. The content of the law is surprisingly clear, as it requires, basically, for all submissions, such as 510(k) information, that proves the device is cyber secure.
Standards and Guidelines
Standards play a crucial role in ensuring harmonized cybersecurity practices across the medical device industry and support the presumption of conformity.
- IEC 81001-5-1 (2021): Published in December 2021, this standard, “Health software and health IT systems safety, effectiveness, and security – Part 5-1: Security – Activities in the product life cycle,” defines lifecycle requirements for secure health software development and maintenance. Adapted from IEC 62443-4-1, it addresses specific needs for health software and is expected to gain Harmonized Standard status under the EU MDR. It complements IEC 62304 and ISO 14971, providing a comprehensive framework for cybersecurity. The standard emphasizes a risk-based approach, requiring manufacturers to identify potential threats and vulnerabilities early through threat modeling and risk assessments. It mandates secure development practices, such as implementing robust coding standards, encryption, and access controls to prevent unauthorized access or tampering. Additionally, it calls for independent security testing to verify the effectiveness of implemented security measures. For the post-market phases, the standard requires ongoing vigilance through continuous monitoring, timely updates, and incident response strategies to address emerging cyber threats.
- ISO 14971:2019: The main requirement of all major legislative acts and guidance documents is the implementation of a security risk management process. In addition, medical device manufacturers are responsible for remaining vigilant to identify all risks and hazards associated with their medical devices, including risks related to cybersecurity. The risk management standard for medical devices was updated in 2019 and includes provisions for data and system security risks, aligning with regulatory requirements for security risk management. The new edition of the risk management standard ISO 14971:2019 can be applied to manage risks associated with data and system security. However, the authors of the standard state that a separate process is not required for managing security risks related to medical devices, which is in line with the specification found in the MDCG guidance.
- ANSI/AAMI SW96:2023: Recognized by the FDA in November 2023, this standard guides medical device security risk management and supports manufacturers in addressing cybersecurity risks. It provides a structured framework for managing cybersecurity risks across the entire lifecycle of medical devices, from design to post-market phases. Building on ISO 14971:2019, it emphasizes identifying and documenting vulnerabilities through threat modeling, evaluating risks in interconnected systems, implementing layered security controls (e.g., encryption, access controls), and maintaining ongoing monitoring and incident response. The FDA encourages the use of this new standard.
Advancements in Cybersecurity Technologies
Technological advancements are shaping the future of medical device cybersecurity, offering both opportunities and challenges:
Artificial Intelligence (AI)
AI is increasingly integrated into medical devices (e.g., for diagnostic purposes) and at the same time used in separate systems to safeguard medical devices through cybersecurity tools, for instance, to protect networks and data flows connected to devices.
AI can analyze device behavior, network traffic to identify unusual patterns that may indicate cyberattacks, hence providing anomaly monitoring and threat detection. AI Models can also predict and anticipate potential security weaknesses. By processing historical data and threat intelligence, it recommends proactive measures, like patching or isolating at-risk devices, before exploits occur. Additionally, AI systems can be designed to identify and counter sophisticated attacks, such as social engineering or source code extraction, by learning from patterns and adapting defenses dynamically. However, while AI offers improved clinical performance and protective benefits, its integration into medical devices introduces new vulnerabilities. AI models are complex, often opaque, and reliant on a vast amount of data, making them targets for attackers. This can expand the attack surface, leading to risks that compromise patient safety, data integrity, and system reliability. Attackers can, for instance, exploit AI through techniques like data poisoning (altering training data to degrade performance) or evasion attacks (crafting inputs to fool the model). For example, experiments have shown that dataset poisoning can reduce ML model accuracy by up to 24%, leading to incorrect diagnoses or treatments in devices like imaging systems [5].
Secure Product Development Framework (SPDF)
Recommended as a key requirement by the FDA, the SPDF is defined as "a set of processes that help identify and reduce the number and severity of vulnerabilities in products". It focuses on security risk management, architecture design, and testing to reduce vulnerabilities and encompasses the entire product lifecycle, including design, development, release, support, and decommissioning. The framework aims to ensure that medical devices are designed securely and can mitigate emerging cybersecurity risks. Key elements are Security Risk Management, Threat Modeling and Vulnerability Assessment, Secure Design and Development Practices, Testing and Validation, Post-Market Monitoring and Maintenance, and Documentation and Transparency. The FDA's SPDF closely correlates with IEC 81001-5-1, as the FDA guidance explicitly references the standard as an example of a framework that can help implement SPDF processes. Both emphasize a lifecycle approach to cybersecurity, integrating security into design, development, and maintenance and ensuring ongoing risk mitigation.
Microsegmentation
This cybersecurity technique creates isolated network segments to improve the security of medical devices. Microsegmentation can significantly strengthen the cybersecurity of medical devices by reducing the ability of attackers to move freely through a hospital network once they gain access to a vulnerable device. Microsegmentation enhances medical device cybersecurity by dividing networks into smaller, isolated segments, limiting the spread of cyberattacks. In a hospital network, if one device or system is compromised, microsegmentation prevents attackers from moving laterally to other devices. It’s particularly effective for protecting legacy devices. Legacy devices often run outdated operating systems, can’t be easily patched (for instance due to regulatory constraints), and may use insecure protocols. Microsegmentation addresses these risks by reducing the network “blast radius” if a breach occurs. IEC 81001-5-1, FDA premarket guidance, and NIS2 encourage least-privilege network design, microsegmentation is one solution to implement such a design.
Conclusion
In the development of connected medical devices, software-driven medical devices, or stand-alone medical software, cybersecurity must be considered from the very early stages of the development. This is necessary, required, and mandatory for market access in Europe, the USA, and all other key markets. At the same time, cybersecurity is a dynamic field requiring constant vigilance and adaptation. The updated regulatory frameworks, standards like IEC 81001-5-1, and technological advancements provide manufacturers with tools to enhance device security. However, recent incidents like the McLaren Health Care cyberattack highlight the persistent threat landscape. By integrating cybersecurity from the early beginning of the development and design to decommissioning, adopting best practices, and staying informed about regulatory changes, manufacturers can protect patients, maintain trust, and ensure compliance in an increasingly connected healthcare ecosystem.
References:
[1] IHS Markit, The Internet of Things: a movement, not a market, e-paper, downloaded 06/14/2021: https://cdn.ihs.com/www/pdf/IoT_ebook.pdf
[2] IQVIA Institute for Human Data Science: The Growing Value of Digital Health, accessed 06/21/2021: https://www.iqvia.com/insights/the-iqvia-institute/reports/the-growing-value-of-digital-health
[3] Irdeto, Global Connected Industries Cybersecurity Survey. IoT Cyberattacks Are The Norm – The Security Mindset Isn’t, downloaded 06/14/2021: https://go.irdeto.com/connected-industries-cybersecurity-survey-report/
[4] Bundesinstitut für Arzneimittel und Medizinprodukte, Cybersicherheit von Medizinprodukten, accessed 06/14/2021: https://www.bfarm.de/DE/Medizinprodukte/RisikoerfassungUndBewertung/Cybersicherheit/kundeninfos_cybersicherheit_node.html
[5] Research Handbook on Health, AI and the Law. Chapter 4Cybersecurity of AI medical devices: risks, legislation, and challenges. https://www.ncbi.nlm.nih.gov/books/NBK613217/
[6] Cybersecurity requirements for medical devices in the EU and US - A comparison and gap analysis of the MDCG 2019–16 and FDA premarket cybersecurity guidance, “Computational and Structural Biotechnology Journal”, Volume 28P259-2662025
[7| “A Way Forward for the MDCG 2019-16 Medical Device Security Guidance”, https://doi.org/10.1145/3652037.3663894
How We Support Your Compliance Journey
Navigating EU and FDA cybersecurity rules is complex. We provide compliance assessments to benchmark practices against MDR, NIS 2, and FDA guidance. With gap analysis and a remediation roadmap, we identify non-compliance and define clear steps to align. Our team supports 510(k), De Novo, and PMA submissions with SBOMs, risk files, and monitoring plans—or delivers a final report with findings, strategies, and long-term compliance recommendations to strengthen cybersecurity across your devices’ lifecycle.